Detecting User Interactions
As described by Singh and Khalid, Upclicker used SetWindowsHookEx to install a hook into the windows messaging subsystem. The hook ID was WH_MOUSE_LL (low level mouse operation) and it filtered for wParam WM_LBUTTONUP (left button up). The malware could also have checked for other input event such as the right mouse button, key strokes; or used the GetLastInputInfo API to determine the number of ticks since the last user interaction of either type. This has been known to work with detecting some sandboxes, but not all. The trick is estimating how many ticks indicate a normal user's "idle" time compared to a sandbox environment. If the delta in tick count exceeds several hours, it may very well be a sandbox system, but then again, if the sandbox developer clicked buttons or pressed keys immediately before taking a snapshot, each time the VM is reverted, it resets the last input tick count to the original value (making it seem like a user was just there).
Anyway, a while back I created a simple test program that checked idle time and I uploaded it to various public sandboxes. It needed a way to convey the value back to me though, which it accomplished by just creating a file named according to the number of idle ticks. The sandbox analysis results would identify the name of the newly created file and that's what I looked at for gathering the info. Unfortunately, this was years ago and I've since lost the data, but the code is below if you want to re-test it and I do remember that several sandboxes reported idle times over a week.
#include <Windows.h>
#include <stdio.h>
int main (int argc, char ** argv)
{
HANDLE hFile;
CHAR szName[MAX_PATH] = {0};
LASTINPUTINFO lii;
lii.cbSize = sizeof(lii);
GetLastInputInfo(&lii);
sprintf(szName, "%d.txt", GetTickCount() - lii.dwTime);
if ((hFile = CreateFileA(szName,
GENERIC_WRITE, 0, NULL,
CREATE_ALWAYS, 0, NULL)) != INVALID_HANDLE_VALUE) {
CloseHandle(hFile);
}
}
Enabling Memory Dumps in Cuckoo Sandbox
To enable memory dumps, edit the conf/cuckoo.conf file and set the memory_dumps field to "on" as shown below:
# Enable creation of memory dump of the analysis machine before shutting
# down. Even if turned off, this functionality can also be enabled at
# submission. Currently available for: VirtualBox and libvirt modules (KVM).
memory_dump = on
As mentioned in the comment, you can leave memory dumps disabled by default and just enable them for a specific submission...but IMO the more memory dumps, the better ;-)
In the case of VirtualBox, the memory dumps are acquired with the dumpguestcore command and are output in the ELF64 core dump format. Volatility parses these files natively starting with 2.3 alpha. Here's the meta-data of the core dump, using the new vboxinfo plugin:
$ ./vol.py -f ~/cuckoo/storage/analyses/10/memory.dmp vboxinfo
Volatile Systems Volatility Framework 2.3_alpha
Magic: 0xc01ac0de
Format: 0x10000
VirtualBox 4.2.4 (revision 81684)
CPUs: 1
File Offset Memory Offset Size
----------- ------------- ----------
0x0000006f0 0x00000000000 0x10000000
0x0100006f0 0x000e0000000 0x02000000
0x0120006f0 0x000f0080000 0x00080000
0x0120806f0 0x000f0400000 0x00400000
0x0124806f0 0x000f0800000 0x00004000
0x0124846f0 0x000ffff0000 0x00010000
Upclicker's First Run
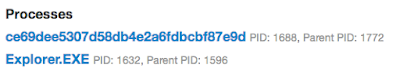
The first time we ran Upclicker in Cuckoo, the results were as expected - no one was there to click the mouse's left button during analysis. Thus there were no dropped files, no mutexes, no modified or created registry values, and it only recorded two API calls from the single Upclicker process:
SetWindowsHookExA is the last API called, because that's when it enters the "waiting" state. As you can see, the HookIdentifier is 14 (0xE) for WH_MOUSE_LL. The ModuleAddress (PE containing the hook procedure) is located at 0x400000. This is a typical ImageBase for the process' executable. The ProcedureAddress (hook function) is at RVA 0x10b0 from the containing PE and the ThreadId was 0 indicating the hook should be applied to all threads in the desktop.
Should you need to validate the API monitor logs, or just analyze the artifacts from a forensic perspective, all of the information should be available in the full memory dump that Cuckoo acquired. To do this, we'll use the messagehooks Volatility plugin:
$ ./vol.py -f ~/cuckoo/storage/analyses/6/memory.dmp messagehooks --output=block
Volatile Systems Volatility Framework 2.3_alpha
Offset(V) : 0xbc64d220
Session : 0
Desktop : WinSta0\Default
Thread : <any>
Filter : WH_MOUSE_LL
Flags : HF_ANSI, HF_GLOBAL
Procedure : 0x10b0
ihmod : 1
Module : C:\DOCUME~1\cooks\LOCALS~1\Temp\ce69dee5307d58db4e2a6fdbcbf87e9d
Offset(V) : 0xbc64d220
Session : 0
Desktop : WinSta0\Default
Thread : 892 (python.exe 1032)
Filter : WH_MOUSE_LL
Flags : HF_ANSI, HF_GLOBAL
Procedure : 0x10b0
ihmod : 1
Module : C:\DOCUME~1\cooks\LOCALS~1\Temp\ce69dee5307d58db4e2a6fdbcbf87e9d
Offset(V) : 0xbc64d220
Session : 0
Desktop : WinSta0\Default
Thread : 1968 (explorer.exe 1632)
Filter : WH_MOUSE_LL
Flags : HF_ANSI, HF_GLOBAL
Procedure : 0x10b0
ihmod : 1
Module : C:\DOCUME~1\cooks\LOCALS~1\Temp\ce69dee5307d58db4e2a6fdbcbf87e9d
Offset(V) : 0xbc64d220
Session : 0
Desktop : WinSta0\Default
Thread : 956 (explorer.exe 1632)
Filter : WH_MOUSE_LL
Flags : HF_ANSI, HF_GLOBAL
Procedure : 0x10b0
ihmod : 1
Module : C:\DOCUME~1\cooks\LOCALS~1\Temp\ce69dee5307d58db4e2a6fdbcbf87e9d
[snip]
There you see the proof of Upclicker's hooks as extracted from physical memory. They are HF_GLOBAL hooks (the result of ThreadId = 0) and they filter WH_MOUSE_LL. The hook procedure is at RVA 0x10b0 of the module which is located on disk at C:\DOCUME~1\cooks\LOCALS~1\Temp\ce69dee5307d58db4e2a6fdbcbf87e9d. This is the binary submitted to Cuckoo - which the sandbox extracts to a temporary directory before executing.
Patching Cuckoo Sandbox
Cuckoo 0.5 is the first version of the framework that I've downloaded and installed. And its been out less than 12 hours, so admittedly I haven't explored much of the code. I did manage to find the analyzer/windows/modules/packages/exe.py file which contains the package for handling executable PEs submitted to the sandbox. I modified the Exe class's start() method such that it sleeps a few seconds after executing the Upclicker process (to allow the SetWindowsHookExA API to finish), then it uses mouse_event to send a MOUSEEVENTF_LEFTUP signal (the left mouse button is up). This should trigger the malware's trap for user interactions and force it to follow through and infect the system.
p = Process()
if not p.execute(path=path, args=args, suspended=suspended):
raise CuckooPackageError("Unable to execute initial process, analysis aborted")
ret = None
if not free and suspended:
p.inject()
p.resume()
ret = p.pid
## just a proof-of-concept, do not actually place
## code here
import ctypes, time
time.sleep(5)
ctypes.windll.USER32.mouse_event(4, # MOUSEEVENTF_LEFTUP
0, # X
0, # Y
0, # no flags
None) # no extra info
return ret
As mentioned in the comment, the Exe package's start() method is undoubtedly the wrong place to put code like this, unless you want it to send a mouse event for all your submissions. But, until I've spent more time getting familiar with the source layout, it'll have to do ;-)
For another example of patching Cuckoo, see Alberto Ortega's Hardening Cuckoo Sandbox against VM aware malware.
Upclicker's Second Run
The second time we ran Upclicker in Cuckoo, the results were much different. First, you can see the signatures detected a new Windows executable was created (dropped) by the malware:
The behavior analysis shows the created file(s). First the submitted sample itself (in the temp directory), then the dropped file named MCPUPlayer.exe which is attached to the system32 directory as an alternate data stream. You also can see the names of the new mutex and registry keys.
Here's a look at Upclicker actually performing the injection:
Now looking at explorer.exe's API calls, you can see it creates an Internet Explorer instance and then injects more code into the IE process.
Hopping from one process to another with code injection isn't anything new. Zeus did it way back in 2006 (and probably was not the first). Next, we'll explore how that appears in memory.
Unpclicker Drops Poison Ivy
Curiosity killed the cat, or curiosity connected the dots - I can't remember what the real saying is. Using Volatility on the memory dump of the infected VM, you can see IEXPLORE.EXE is pid 1740.
$ ./vol.py -f ~/cuckoo/storage/analyses/10/memory.dmp pslist
Volatile Systems Volatility Framework 2.3_alpha
Offset(V) Name PID PPID Thds Hnds Start
---------- -------------- ------ ------ ------ -------- ----------------------
0x819cc9c8 System 4 0 54 263
0x817d54a8 smss.exe 536 4 3 19 2012-12-20 03:33:17
0x817a1020 csrss.exe 584 536 11 349 2012-12-20 03:33:18
0x81799020 winlogon.exe 616 536 18 509 2012-12-20 03:33:19
0x8176f020 services.exe 660 616 15 242 2012-12-20 03:33:19
[snip]
0x81617058 cmd.exe 1116 1632 1 33 2012-12-20 03:35:22
0x816c9020 python.exe 1032 1116 1 93 2012-12-21 02:55:00
0x815c7910 IEXPLORE.EXE 1740 1632 3 76 2012-12-21 04:14:13
If there's injected code, we should be able to find it pretty easily. In fact, the malfind plugin located 20+ suspicious segments of memory - each which contain what looks like the beginning of a function.
$ ./vol.py -f ~/Desktop/cuckoo/storage/analyses/10/memory.dmp malfind -p 1740 Volatile Systems Volatility Framework 2.3_alpha Process: IEXPLORE.EXE Pid: 1740 Address: 0xa70000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00a70000 55 8b ec 50 b8 10 00 00 00 81 c4 04 f0 ff ff 50 U..P...........P 0x00a70010 48 75 f6 8b 45 fc 81 c4 48 fe ff ff 53 56 57 8b Hu..E...H...SVW. 0x00a70020 45 08 89 45 bc 8b 45 bc 8b 80 b4 08 00 00 8b f8 E..E..E......... 0x00a70030 8b 40 34 89 45 b8 8b 45 b8 8b 80 24 03 00 00 89 .@4.E..E...$.... 0xa70000 55 PUSH EBP 0xa70001 8bec MOV EBP, ESP 0xa70003 50 PUSH EAX 0xa70004 b810000000 MOV EAX, 0x10 0xa70009 81c404f0ffff ADD ESP, 0xfffff004 0xa7000f 50 PUSH EAX 0xa70010 48 DEC EAX 0xa70011 75f6 JNZ 0xa70009 0xa70013 8b45fc MOV EAX, [EBP+0xfffffffc] 0xa70016 81c448feffff ADD ESP, 0xfffffe48 0xa7001c 53 PUSH EBX 0xa7001d 56 PUSH ESI 0xa7001e 57 PUSH EDI 0xa7001f 8b4508 MOV EAX, [EBP+0x8] 0xa70022 8945bc MOV [EBP+0xffffffbc], EAX 0xa70025 8b45bc MOV EAX, [EBP+0xffffffbc] 0xa70028 8b80b4080000 MOV EAX, [EAX+0x8b4] 0xa7002e 8bf8 MOV EDI, EAX 0xa70030 8b4034 MOV EAX, [EAX+0x34] 0xa70033 8945b8 MOV [EBP+0xffffffb8], EAX 0xa70036 8b45b8 MOV EAX, [EBP+0xffffffb8] 0xa70039 8b8024030000 MOV EAX, [EAX+0x324] 0xa7003f 89 DB 0x89 Process: IEXPLORE.EXE Pid: 1740 Address: 0xa30000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 2, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00a30000 55 8b ec 50 b8 10 00 00 00 81 c4 04 f0 ff ff 50 U..P...........P 0x00a30010 48 75 f6 8b 45 fc 83 c4 b8 53 56 57 8b 75 08 33 Hu..E....SVW.u.3 0x00a30020 c0 89 86 b9 08 00 00 33 c0 89 45 e4 68 4d 4b 58 .......3..E.hMKX 0x00a30030 5a 8b 86 db 0a 00 00 50 8b 86 e1 00 00 00 50 ff Z......P......P. 0xa30000 55 PUSH EBP 0xa30001 8bec MOV EBP, ESP 0xa30003 50 PUSH EAX 0xa30004 b810000000 MOV EAX, 0x10 0xa30009 81c404f0ffff ADD ESP, 0xfffff004 0xa3000f 50 PUSH EAX 0xa30010 48 DEC EAX 0xa30011 75f6 JNZ 0xa30009 0xa30013 8b45fc MOV EAX, [EBP+0xfffffffc] 0xa30016 83c4b8 ADD ESP, -0x48 0xa30019 53 PUSH EBX 0xa3001a 56 PUSH ESI 0xa3001b 57 PUSH EDI 0xa3001c 8b7508 MOV ESI, [EBP+0x8] 0xa3001f 33c0 XOR EAX, EAX 0xa30021 8986b9080000 MOV [ESI+0x8b9], EAX 0xa30027 33c0 XOR EAX, EAX 0xa30029 8945e4 MOV [EBP+0xffffffe4], EAX 0xa3002c 684d4b585a PUSH DWORD 0x5a584b4d 0xa30031 8b86db0a0000 MOV EAX, [ESI+0xadb] 0xa30037 50 PUSH EAX 0xa30038 8b86e1000000 MOV EAX, [ESI+0xe1] 0xa3003e 50 PUSH EAX 0xa3003f ff DB 0xff Process: IEXPLORE.EXE Pid: 1740 Address: 0x160000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00160000 00 11 42 ab 71 07 4a ab 71 2b 3e ab 71 27 4c ab ..B.q.J.q+>.q'L. 0x00160010 71 6f 67 ab 71 53 2e ab 71 e1 2e ab 71 55 53 ab qog.qS..q...qUS. 0x00160020 71 e1 9a 80 7c 74 9b 80 7c c7 06 81 7c 6b 23 80 q...|t..|...|k#. 0x00160030 7c 17 6c dd 77 42 78 dd 77 ab 7a dd 77 d7 ea dd |.l.wBx.w.z.w... 0x160000 0011 ADD [ECX], DL 0x160002 42 INC EDX 0x160003 ab STOSD 0x160004 7107 JNO 0x16000d 0x160006 4a DEC EDX 0x160007 ab STOSD 0x160008 712b JNO 0x160035 0x16000a 3eab STOSD 0x16000c 7127 JNO 0x160035 0x16000e 4c DEC ESP 0x16000f ab STOSD 0x160010 716f JNO 0x160081 0x160012 67ab STOS [ES:DI], EAX 0x160014 7153 JNO 0x160069 0x160016 2eab STOSD 0x160018 71e1 JNO 0x15fffb 0x16001a 2eab STOSD 0x16001c 7155 JNO 0x160073 0x16001e 53 PUSH EBX 0x16001f ab STOSD 0x160020 71e1 JNO 0x160003 0x160022 9a807c749b807c CALL FAR 0x7c80:0x9b747c80 0x160029 c706817c6b23 MOV DWORD [ESI], 0x236b7c81 0x16002f 807c176cdd CMP BYTE [EDI+EDX+0x6c], 0xdd 0x160034 7742 JA 0x160078 0x160036 78dd JS 0x160015 0x160038 77ab JA 0x15ffe5 0x16003a 7add JP 0x160019 0x16003c 77d7 JA 0x160015 0x16003e ea DB 0xea 0x16003f dd DB 0xdd Process: IEXPLORE.EXE Pid: 1740 Address: 0x150000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00150000 55 8b ec 81 c4 30 fa ff ff 8b 75 08 8d 86 fb 03 U....0....u..... 0x00150010 00 00 50 6a 00 6a 00 ff 96 85 00 00 00 89 86 c5 ..Pj.j.......... 0x00150020 08 00 00 ff 96 89 00 00 00 3d b7 00 00 00 75 04 .........=....u. 0x00150030 c9 c2 04 00 56 8d 86 6b 09 00 00 50 8d 86 45 01 ....V..k...P..E. 0x150000 55 PUSH EBP 0x150001 8bec MOV EBP, ESP 0x150003 81c430faffff ADD ESP, 0xfffffa30 0x150009 8b7508 MOV ESI, [EBP+0x8] 0x15000c 8d86fb030000 LEA EAX, [ESI+0x3fb] 0x150012 50 PUSH EAX 0x150013 6a00 PUSH 0x0 0x150015 6a00 PUSH 0x0 0x150017 ff9685000000 CALL DWORD [ESI+0x85] 0x15001d 8986c5080000 MOV [ESI+0x8c5], EAX 0x150023 ff9689000000 CALL DWORD [ESI+0x89] 0x150029 3db7000000 CMP EAX, 0xb7 0x15002e 7504 JNZ 0x150034 0x150030 c9 LEAVE 0x150031 c20400 RET 0x4 0x150034 56 PUSH ESI 0x150035 8d866b090000 LEA EAX, [ESI+0x96b] 0x15003b 50 PUSH EAX 0x15003c 8d DB 0x8d 0x15003d 864501 XCHG [EBP+0x1], AL Process: IEXPLORE.EXE Pid: 1740 Address: 0xa50000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00a50000 00 00 00 00 00 00 00 00 00 00 c5 00 00 00 cc 00 ................ 0x00a50010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x00a50020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x00a50030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xa50000 0000 ADD [EAX], AL 0xa50002 0000 ADD [EAX], AL 0xa50004 0000 ADD [EAX], AL 0xa50006 0000 ADD [EAX], AL 0xa50008 0000 ADD [EAX], AL 0xa5000a c500 LDS EAX, [EAX] 0xa5000c 0000 ADD [EAX], AL 0xa5000e cc INT 3 0xa5000f 0000 ADD [EAX], AL 0xa50011 0000 ADD [EAX], AL 0xa50013 0000 ADD [EAX], AL 0xa50015 0000 ADD [EAX], AL 0xa50017 0000 ADD [EAX], AL 0xa50019 0000 ADD [EAX], AL 0xa5001b 0000 ADD [EAX], AL 0xa5001d 0000 ADD [EAX], AL 0xa5001f 0000 ADD [EAX], AL 0xa50021 0000 ADD [EAX], AL 0xa50023 0000 ADD [EAX], AL 0xa50025 0000 ADD [EAX], AL 0xa50027 0000 ADD [EAX], AL 0xa50029 0000 ADD [EAX], AL 0xa5002b 0000 ADD [EAX], AL 0xa5002d 0000 ADD [EAX], AL 0xa5002f 0000 ADD [EAX], AL 0xa50031 0000 ADD [EAX], AL 0xa50033 0000 ADD [EAX], AL 0xa50035 0000 ADD [EAX], AL 0xa50037 0000 ADD [EAX], AL 0xa50039 0000 ADD [EAX], AL 0xa5003b 0000 ADD [EAX], AL 0xa5003d 0000 ADD [EAX], AL 0xa5003f 00 DB 0x0 Process: IEXPLORE.EXE Pid: 1740 Address: 0xa40000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00a40000 e8 00 00 00 60 38 1c 00 ff ff ff ff 00 00 00 00 ....`8.......... 0x00a40010 00 00 00 00 00 00 00 00 00 00 00 00 d0 3f 1c 00 .............?.. 0x00a40020 ff ff ff ff 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x00a40030 00 00 00 00 00 00 a5 00 00 00 00 00 01 00 00 00 ................ 0xa40000 e800000060 CALL 0x60a40005 0xa40005 381c00 CMP [EAX+EAX], BL 0xa40008 ff DB 0xff 0xa40009 ff DB 0xff 0xa4000a ff DB 0xff 0xa4000b ff00 INC DWORD [EAX] 0xa4000d 0000 ADD [EAX], AL 0xa4000f 0000 ADD [EAX], AL 0xa40011 0000 ADD [EAX], AL 0xa40013 0000 ADD [EAX], AL 0xa40015 0000 ADD [EAX], AL 0xa40017 0000 ADD [EAX], AL 0xa40019 0000 ADD [EAX], AL 0xa4001b 00d0 ADD AL, DL 0xa4001d 3f AAS 0xa4001e 1c00 SBB AL, 0x0 0xa40020 ff DB 0xff 0xa40021 ff DB 0xff 0xa40022 ff DB 0xff 0xa40023 ff00 INC DWORD [EAX] 0xa40025 0000 ADD [EAX], AL 0xa40027 0000 ADD [EAX], AL 0xa40029 0000 ADD [EAX], AL 0xa4002b 0000 ADD [EAX], AL 0xa4002d 0000 ADD [EAX], AL 0xa4002f 0000 ADD [EAX], AL 0xa40031 0000 ADD [EAX], AL 0xa40033 0000 ADD [EAX], AL 0xa40035 00a500000000 ADD [EBP+0x0], AH 0xa4003b 0001 ADD [ECX], AL 0xa4003d 0000 ADD [EAX], AL 0xa4003f 00 DB 0x0 Process: IEXPLORE.EXE Pid: 1740 Address: 0xa60000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00a60000 55 8b ec 83 c4 c8 53 56 57 8b 5d 08 8b 73 08 33 U.....SVW.]..s.3 0x00a60010 c0 89 45 f0 c6 45 e3 00 80 be b8 08 00 00 00 0f ..E..E.......... 0x00a60020 84 b2 00 00 00 c6 86 b8 08 00 00 00 8b 86 b4 08 ................ 0x00a60030 00 00 33 d2 89 50 38 6a 01 8b 03 03 45 f0 50 8d ..3..P8j....E.P. 0xa60000 55 PUSH EBP 0xa60001 8bec MOV EBP, ESP 0xa60003 83c4c8 ADD ESP, -0x38 0xa60006 53 PUSH EBX 0xa60007 56 PUSH ESI 0xa60008 57 PUSH EDI 0xa60009 8b5d08 MOV EBX, [EBP+0x8] 0xa6000c 8b7308 MOV ESI, [EBX+0x8] 0xa6000f 33c0 XOR EAX, EAX 0xa60011 8945f0 MOV [EBP+0xfffffff0], EAX 0xa60014 c645e300 MOV BYTE [EBP+0xffffffe3], 0x0 0xa60018 80beb808000000 CMP BYTE [ESI+0x8b8], 0x0 0xa6001f 0f84b2000000 JZ 0xa600d7 0xa60025 c686b808000000 MOV BYTE [ESI+0x8b8], 0x0 0xa6002c 8b86b4080000 MOV EAX, [ESI+0x8b4] 0xa60032 33d2 XOR EDX, EDX 0xa60034 895038 MOV [EAX+0x38], EDX 0xa60037 6a01 PUSH 0x1 0xa60039 8b03 MOV EAX, [EBX] 0xa6003b 0345f0 ADD EAX, [EBP+0xfffffff0] 0xa6003e 50 PUSH EAX 0xa6003f 8d DB 0x8d Process: IEXPLORE.EXE Pid: 1740 Address: 0xc50000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00c50000 55 8b ec 83 c4 cc 53 56 57 89 4d dc 89 55 e0 33 U.....SVW.M..U.3 0x00c50010 d2 8b f8 8b 87 b4 08 00 00 8b f0 8b 40 34 89 45 ............@4.E 0x00c50020 cc 8b 45 cc 8b 80 24 03 00 00 89 45 e8 8b 45 cc ..E...$....E..E. 0x00c50030 8b 40 08 05 b0 01 00 00 89 45 e4 64 ff 35 00 00 .@.......E.d.5.. 0xc50000 55 PUSH EBP 0xc50001 8bec MOV EBP, ESP 0xc50003 83c4cc ADD ESP, -0x34 0xc50006 53 PUSH EBX 0xc50007 56 PUSH ESI 0xc50008 57 PUSH EDI 0xc50009 894ddc MOV [EBP+0xffffffdc], ECX 0xc5000c 8955e0 MOV [EBP+0xffffffe0], EDX 0xc5000f 33d2 XOR EDX, EDX 0xc50011 8bf8 MOV EDI, EAX 0xc50013 8b87b4080000 MOV EAX, [EDI+0x8b4] 0xc50019 8bf0 MOV ESI, EAX 0xc5001b 8b4034 MOV EAX, [EAX+0x34] 0xc5001e 8945cc MOV [EBP+0xffffffcc], EAX 0xc50021 8b45cc MOV EAX, [EBP+0xffffffcc] 0xc50024 8b8024030000 MOV EAX, [EAX+0x324] 0xc5002a 8945e8 MOV [EBP+0xffffffe8], EAX 0xc5002d 8b45cc MOV EAX, [EBP+0xffffffcc] 0xc50030 8b4008 MOV EAX, [EAX+0x8] 0xc50033 05b0010000 ADD EAX, 0x1b0 0xc50038 8945e4 MOV [EBP+0xffffffe4], EAX 0xc5003b 64 DB 0x64 0xc5003c ff DB 0xff 0xc5003d 35 DB 0x35 0xc5003e 0000 ADD [EAX], AL Process: IEXPLORE.EXE Pid: 1740 Address: 0xc70000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00c70000 53 56 8b c8 8b 99 b4 08 00 00 8b 73 34 8b da 33 SV.........s4..3 0x00c70010 c9 ff 96 d4 01 00 00 33 c0 89 43 04 33 c0 89 43 .......3..C.3..C 0x00c70020 08 5e 5b c3 00 00 00 00 00 00 00 00 00 00 00 00 .^[............. 0x00c70030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xc70000 53 PUSH EBX 0xc70001 56 PUSH ESI 0xc70002 8bc8 MOV ECX, EAX 0xc70004 8b99b4080000 MOV EBX, [ECX+0x8b4] 0xc7000a 8b7334 MOV ESI, [EBX+0x34] 0xc7000d 8bda MOV EBX, EDX 0xc7000f 33c9 XOR ECX, ECX 0xc70011 ff96d4010000 CALL DWORD [ESI+0x1d4] 0xc70017 33c0 XOR EAX, EAX 0xc70019 894304 MOV [EBX+0x4], EAX 0xc7001c 33c0 XOR EAX, EAX 0xc7001e 894308 MOV [EBX+0x8], EAX 0xc70021 5e POP ESI 0xc70022 5b POP EBX 0xc70023 c3 RET 0xc70024 0000 ADD [EAX], AL 0xc70026 0000 ADD [EAX], AL 0xc70028 0000 ADD [EAX], AL 0xc7002a 0000 ADD [EAX], AL 0xc7002c 0000 ADD [EAX], AL 0xc7002e 0000 ADD [EAX], AL 0xc70030 0000 ADD [EAX], AL 0xc70032 0000 ADD [EAX], AL 0xc70034 0000 ADD [EAX], AL 0xc70036 0000 ADD [EAX], AL 0xc70038 0000 ADD [EAX], AL 0xc7003a 0000 ADD [EAX], AL 0xc7003c 0000 ADD [EAX], AL 0xc7003e 0000 ADD [EAX], AL Process: IEXPLORE.EXE Pid: 1740 Address: 0xc60000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00c60000 55 8b ec 83 c4 e4 53 56 57 8b 5d 10 8b 45 08 8b U.....SVW.]..E.. 0x00c60010 90 b4 08 00 00 8b 72 34 8b 86 24 03 00 00 89 45 ......r4..$....E 0x00c60020 e8 8b 86 d8 01 00 00 05 e0 00 00 00 89 45 e4 64 .............E.d 0x00c60030 ff 35 00 00 00 00 8f 45 ec ff 75 e8 8f 45 f0 ff .5.....E..u..E.. 0xc60000 55 PUSH EBP 0xc60001 8bec MOV EBP, ESP 0xc60003 83c4e4 ADD ESP, -0x1c 0xc60006 53 PUSH EBX 0xc60007 56 PUSH ESI 0xc60008 57 PUSH EDI 0xc60009 8b5d10 MOV EBX, [EBP+0x10] 0xc6000c 8b4508 MOV EAX, [EBP+0x8] 0xc6000f 8b90b4080000 MOV EDX, [EAX+0x8b4] 0xc60015 8b7234 MOV ESI, [EDX+0x34] 0xc60018 8b8624030000 MOV EAX, [ESI+0x324] 0xc6001e 8945e8 MOV [EBP+0xffffffe8], EAX 0xc60021 8b86d8010000 MOV EAX, [ESI+0x1d8] 0xc60027 05e0000000 ADD EAX, 0xe0 0xc6002c 8945e4 MOV [EBP+0xffffffe4], EAX 0xc6002f 64ff3500000000 PUSH DWORD [FS:0x0] 0xc60036 8f45ec POP DWORD [EBP+0xffffffec] 0xc60039 ff75e8 PUSH DWORD [EBP+0xffffffe8] 0xc6003c 8f45f0 POP DWORD [EBP+0xfffffff0] 0xc6003f ff DB 0xff Process: IEXPLORE.EXE Pid: 1740 Address: 0xc90000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00c90000 55 8b ec 51 53 56 57 8b 7d 0c 8b 55 08 8b f2 8b U..QSVW.}..U.... 0x00c90010 86 b4 08 00 00 8b 40 34 8b df 83 7b 08 00 7c 56 ......@4...{..|V 0x00c90020 83 7d 14 00 7c 50 8b 4b 08 03 4d 14 89 4d fc 83 .}..|P.K..M..M.. 0x00c90030 7d fc 00 7e 41 8b 4d fc 3b 4b 04 7e 1a 8b 4d fc }..~A.M.;K.~..M. 0xc90000 55 PUSH EBP 0xc90001 8bec MOV EBP, ESP 0xc90003 51 PUSH ECX 0xc90004 53 PUSH EBX 0xc90005 56 PUSH ESI 0xc90006 57 PUSH EDI 0xc90007 8b7d0c MOV EDI, [EBP+0xc] 0xc9000a 8b5508 MOV EDX, [EBP+0x8] 0xc9000d 8bf2 MOV ESI, EDX 0xc9000f 8b86b4080000 MOV EAX, [ESI+0x8b4] 0xc90015 8b4034 MOV EAX, [EAX+0x34] 0xc90018 8bdf MOV EBX, EDI 0xc9001a 837b0800 CMP DWORD [EBX+0x8], 0x0 0xc9001e 7c56 JL 0xc90076 0xc90020 837d1400 CMP DWORD [EBP+0x14], 0x0 0xc90024 7c50 JL 0xc90076 0xc90026 8b4b08 MOV ECX, [EBX+0x8] 0xc90029 034d14 ADD ECX, [EBP+0x14] 0xc9002c 894dfc MOV [EBP+0xfffffffc], ECX 0xc9002f 837dfc00 CMP DWORD [EBP+0xfffffffc], 0x0 0xc90033 7e41 JLE 0xc90076 0xc90035 8b4dfc MOV ECX, [EBP+0xfffffffc] 0xc90038 3b4b04 CMP ECX, [EBX+0x4] 0xc9003b 7e1a JLE 0xc90057 0xc9003d 8b4dfc MOV ECX, [EBP+0xfffffffc] Process: IEXPLORE.EXE Pid: 1740 Address: 0xc80000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00c80000 53 56 8b c8 8b 99 b4 08 00 00 8b 73 34 8b ca 33 SV.........s4..3 0x00c80010 db 89 19 33 db 89 59 04 33 db 89 59 08 33 db 89 ...3..Y.3..Y.3.. 0x00c80020 59 0c 33 c9 ff 96 d4 01 00 00 5e 5b c3 00 00 00 Y.3.......^[.... 0x00c80030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xc80000 53 PUSH EBX 0xc80001 56 PUSH ESI 0xc80002 8bc8 MOV ECX, EAX 0xc80004 8b99b4080000 MOV EBX, [ECX+0x8b4] 0xc8000a 8b7334 MOV ESI, [EBX+0x34] 0xc8000d 8bca MOV ECX, EDX 0xc8000f 33db XOR EBX, EBX 0xc80011 8919 MOV [ECX], EBX 0xc80013 33db XOR EBX, EBX 0xc80015 895904 MOV [ECX+0x4], EBX 0xc80018 33db XOR EBX, EBX 0xc8001a 895908 MOV [ECX+0x8], EBX 0xc8001d 33db XOR EBX, EBX 0xc8001f 89590c MOV [ECX+0xc], EBX 0xc80022 33c9 XOR ECX, ECX 0xc80024 ff96d4010000 CALL DWORD [ESI+0x1d4] 0xc8002a 5e POP ESI 0xc8002b 5b POP EBX 0xc8002c c3 RET 0xc8002d 0000 ADD [EAX], AL 0xc8002f 0000 ADD [EAX], AL 0xc80031 0000 ADD [EAX], AL 0xc80033 0000 ADD [EAX], AL 0xc80035 0000 ADD [EAX], AL 0xc80037 0000 ADD [EAX], AL 0xc80039 0000 ADD [EAX], AL 0xc8003b 0000 ADD [EAX], AL 0xc8003d 0000 ADD [EAX], AL 0xc8003f 00 DB 0x0 Process: IEXPLORE.EXE Pid: 1740 Address: 0xcb0000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00cb0000 53 56 57 55 51 89 0c 24 8b fa 8b f0 8b c6 8b 90 SVWUQ..$........ 0x00cb0010 b4 08 00 00 8b 6a 34 8b df 54 57 56 ff 95 d8 01 .....j4..TWV.... 0x00cb0020 00 00 89 03 8b 04 24 89 43 0c 5a 5d 5f 5e 5b c3 ......$.C.Z]_^[. 0x00cb0030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xcb0000 53 PUSH EBX 0xcb0001 56 PUSH ESI 0xcb0002 57 PUSH EDI 0xcb0003 55 PUSH EBP 0xcb0004 51 PUSH ECX 0xcb0005 890c24 MOV [ESP], ECX 0xcb0008 8bfa MOV EDI, EDX 0xcb000a 8bf0 MOV ESI, EAX 0xcb000c 8bc6 MOV EAX, ESI 0xcb000e 8b90b4080000 MOV EDX, [EAX+0x8b4] 0xcb0014 8b6a34 MOV EBP, [EDX+0x34] 0xcb0017 8bdf MOV EBX, EDI 0xcb0019 54 PUSH ESP 0xcb001a 57 PUSH EDI 0xcb001b 56 PUSH ESI 0xcb001c ff95d8010000 CALL DWORD [EBP+0x1d8] 0xcb0022 8903 MOV [EBX], EAX 0xcb0024 8b0424 MOV EAX, [ESP] 0xcb0027 89430c MOV [EBX+0xc], EAX 0xcb002a 5a POP EDX 0xcb002b 5d POP EBP 0xcb002c 5f POP EDI 0xcb002d 5e POP ESI 0xcb002e 5b POP EBX 0xcb002f c3 RET 0xcb0030 0000 ADD [EAX], AL 0xcb0032 0000 ADD [EAX], AL 0xcb0034 0000 ADD [EAX], AL 0xcb0036 0000 ADD [EAX], AL 0xcb0038 0000 ADD [EAX], AL 0xcb003a 0000 ADD [EAX], AL 0xcb003c 0000 ADD [EAX], AL 0xcb003e 0000 ADD [EAX], AL Process: IEXPLORE.EXE Pid: 1740 Address: 0xca0000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00ca0000 55 8b ec 83 c4 e4 53 56 57 8b 7d 14 8b 55 08 8b U.....SVW.}..U.. 0x00ca0010 82 b4 08 00 00 8b 40 34 8b 88 24 03 00 00 89 4d ......@4..$....M 0x00ca0020 e8 8b 80 d0 01 00 00 05 88 00 00 00 89 45 e4 64 .............E.d 0x00ca0030 ff 35 00 00 00 00 8f 45 ec ff 75 e8 8f 45 f0 ff .5.....E..u..E.. 0xca0000 55 PUSH EBP 0xca0001 8bec MOV EBP, ESP 0xca0003 83c4e4 ADD ESP, -0x1c 0xca0006 53 PUSH EBX 0xca0007 56 PUSH ESI 0xca0008 57 PUSH EDI 0xca0009 8b7d14 MOV EDI, [EBP+0x14] 0xca000c 8b5508 MOV EDX, [EBP+0x8] 0xca000f 8b82b4080000 MOV EAX, [EDX+0x8b4] 0xca0015 8b4034 MOV EAX, [EAX+0x34] 0xca0018 8b8824030000 MOV ECX, [EAX+0x324] 0xca001e 894de8 MOV [EBP+0xffffffe8], ECX 0xca0021 8b80d0010000 MOV EAX, [EAX+0x1d0] 0xca0027 0588000000 ADD EAX, 0x88 0xca002c 8945e4 MOV [EBP+0xffffffe4], EAX 0xca002f 64ff3500000000 PUSH DWORD [FS:0x0] 0xca0036 8f45ec POP DWORD [EBP+0xffffffec] 0xca0039 ff75e8 PUSH DWORD [EBP+0xffffffe8] 0xca003c 8f45f0 POP DWORD [EBP+0xfffffff0] 0xca003f ff DB 0xff Process: IEXPLORE.EXE Pid: 1740 Address: 0xcc0000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00cc0000 55 8b ec 81 c4 b0 fe ff ff 53 56 57 8b fa 89 45 U........SVW...E 0x00cc0010 d8 8b 75 d8 8b 86 b4 08 00 00 8b 58 34 8b 83 24 ..u........X4..$ 0x00cc0020 03 00 00 89 45 e8 8b 43 0c 05 c9 04 00 00 89 45 ....E..C.......E 0x00cc0030 e4 64 ff 35 00 00 00 00 8f 45 ec ff 75 e8 8f 45 .d.5.....E..u..E 0xcc0000 55 PUSH EBP 0xcc0001 8bec MOV EBP, ESP 0xcc0003 81c4b0feffff ADD ESP, 0xfffffeb0 0xcc0009 53 PUSH EBX 0xcc000a 56 PUSH ESI 0xcc000b 57 PUSH EDI 0xcc000c 8bfa MOV EDI, EDX 0xcc000e 8945d8 MOV [EBP+0xffffffd8], EAX 0xcc0011 8b75d8 MOV ESI, [EBP+0xffffffd8] 0xcc0014 8b86b4080000 MOV EAX, [ESI+0x8b4] 0xcc001a 8b5834 MOV EBX, [EAX+0x34] 0xcc001d 8b8324030000 MOV EAX, [EBX+0x324] 0xcc0023 8945e8 MOV [EBP+0xffffffe8], EAX 0xcc0026 8b430c MOV EAX, [EBX+0xc] 0xcc0029 05c9040000 ADD EAX, 0x4c9 0xcc002e 8945e4 MOV [EBP+0xffffffe4], EAX 0xcc0031 64ff3500000000 PUSH DWORD [FS:0x0] 0xcc0038 8f45ec POP DWORD [EBP+0xffffffec] 0xcc003b ff75e8 PUSH DWORD [EBP+0xffffffe8] 0xcc003e 8f DB 0x8f 0xcc003f 45 INC EBP Process: IEXPLORE.EXE Pid: 1740 Address: 0xcd0000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00cd0000 55 8b ec 83 c4 80 53 56 57 89 4d d8 89 55 dc 89 U.....SVW.M..U.. 0x00cd0010 45 e0 8b 5d 08 8b 45 e0 89 45 c0 8b 45 c0 8b 80 E..]..E..E..E... 0x00cd0020 b4 08 00 00 89 45 bc 8b 70 34 8b 86 24 03 00 00 .....E..p4..$... 0x00cd0030 89 45 e8 8b 46 58 05 6e 03 00 00 89 45 e4 64 ff .E..FX.n....E.d. 0xcd0000 55 PUSH EBP 0xcd0001 8bec MOV EBP, ESP 0xcd0003 83c480 ADD ESP, -0x80 0xcd0006 53 PUSH EBX 0xcd0007 56 PUSH ESI 0xcd0008 57 PUSH EDI 0xcd0009 894dd8 MOV [EBP+0xffffffd8], ECX 0xcd000c 8955dc MOV [EBP+0xffffffdc], EDX 0xcd000f 8945e0 MOV [EBP+0xffffffe0], EAX 0xcd0012 8b5d08 MOV EBX, [EBP+0x8] 0xcd0015 8b45e0 MOV EAX, [EBP+0xffffffe0] 0xcd0018 8945c0 MOV [EBP+0xffffffc0], EAX 0xcd001b 8b45c0 MOV EAX, [EBP+0xffffffc0] 0xcd001e 8b80b4080000 MOV EAX, [EAX+0x8b4] 0xcd0024 8945bc MOV [EBP+0xffffffbc], EAX 0xcd0027 8b7034 MOV ESI, [EAX+0x34] 0xcd002a 8b8624030000 MOV EAX, [ESI+0x324] 0xcd0030 8945e8 MOV [EBP+0xffffffe8], EAX 0xcd0033 8b4658 MOV EAX, [ESI+0x58] 0xcd0036 056e030000 ADD EAX, 0x36e 0xcd003b 8945e4 MOV [EBP+0xffffffe4], EAX 0xcd003e 64 DB 0x64 0xcd003f ff DB 0xff Process: IEXPLORE.EXE Pid: 1740 Address: 0xcf0000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00cf0000 55 8b ec 83 c4 a4 53 56 57 89 55 dc 89 45 e0 8b U.....SVW.U..E.. 0x00cf0010 45 e0 8b 90 b4 08 00 00 8b 5a 34 8b 83 24 03 00 E........Z4..$.. 0x00cf0020 00 89 45 e8 8b 83 54 04 00 00 05 41 01 00 00 89 ..E...T....A.... 0x00cf0030 45 e4 64 ff 35 00 00 00 00 8f 45 ec ff 75 e8 8f E.d.5.....E..u.. 0xcf0000 55 PUSH EBP 0xcf0001 8bec MOV EBP, ESP 0xcf0003 83c4a4 ADD ESP, -0x5c 0xcf0006 53 PUSH EBX 0xcf0007 56 PUSH ESI 0xcf0008 57 PUSH EDI 0xcf0009 8955dc MOV [EBP+0xffffffdc], EDX 0xcf000c 8945e0 MOV [EBP+0xffffffe0], EAX 0xcf000f 8b45e0 MOV EAX, [EBP+0xffffffe0] 0xcf0012 8b90b4080000 MOV EDX, [EAX+0x8b4] 0xcf0018 8b5a34 MOV EBX, [EDX+0x34] 0xcf001b 8b8324030000 MOV EAX, [EBX+0x324] 0xcf0021 8945e8 MOV [EBP+0xffffffe8], EAX 0xcf0024 8b8354040000 MOV EAX, [EBX+0x454] 0xcf002a 0541010000 ADD EAX, 0x141 0xcf002f 8945e4 MOV [EBP+0xffffffe4], EAX 0xcf0032 64ff3500000000 PUSH DWORD [FS:0x0] 0xcf0039 8f45ec POP DWORD [EBP+0xffffffec] 0xcf003c ff75e8 PUSH DWORD [EBP+0xffffffe8] 0xcf003f 8f DB 0x8f Process: IEXPLORE.EXE Pid: 1740 Address: 0xd00000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00d00000 53 56 57 55 51 8b e9 8b fa 8b f0 8b c6 8b 90 b4 SVWUQ........... 0x00d00010 08 00 00 8b 5a 34 55 ff 53 70 88 04 24 6a 01 8d ....Z4U.Sp..$j.. 0x00d00020 44 24 04 50 57 56 ff 93 cc 01 00 00 33 c0 8a 04 D$.PWV......3... 0x00d00030 24 50 55 57 56 ff 93 cc 01 00 00 5a 5d 5f 5e 5b $PUWV......Z]_^[ 0xd00000 53 PUSH EBX 0xd00001 56 PUSH ESI 0xd00002 57 PUSH EDI 0xd00003 55 PUSH EBP 0xd00004 51 PUSH ECX 0xd00005 8be9 MOV EBP, ECX 0xd00007 8bfa MOV EDI, EDX 0xd00009 8bf0 MOV ESI, EAX 0xd0000b 8bc6 MOV EAX, ESI 0xd0000d 8b90b4080000 MOV EDX, [EAX+0x8b4] 0xd00013 8b5a34 MOV EBX, [EDX+0x34] 0xd00016 55 PUSH EBP 0xd00017 ff5370 CALL DWORD [EBX+0x70] 0xd0001a 880424 MOV [ESP], AL 0xd0001d 6a01 PUSH 0x1 0xd0001f 8d442404 LEA EAX, [ESP+0x4] 0xd00023 50 PUSH EAX 0xd00024 57 PUSH EDI 0xd00025 56 PUSH ESI 0xd00026 ff93cc010000 CALL DWORD [EBX+0x1cc] 0xd0002c 33c0 XOR EAX, EAX 0xd0002e 8a0424 MOV AL, [ESP] 0xd00031 50 PUSH EAX 0xd00032 55 PUSH EBP 0xd00033 57 PUSH EDI 0xd00034 56 PUSH ESI 0xd00035 ff93cc010000 CALL DWORD [EBX+0x1cc] 0xd0003b 5a POP EDX 0xd0003c 5d POP EBP 0xd0003d 5f POP EDI 0xd0003e 5e POP ESI 0xd0003f 5b POP EBX Process: IEXPLORE.EXE Pid: 1740 Address: 0xd10000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00d10000 55 8b ec 8b 55 10 8b 45 0c 8b 48 08 89 8a b8 00 U...U..E..H..... 0x00d10010 00 00 8b 48 0c 89 8a c4 00 00 00 8b 40 10 89 82 ...H........@... 0x00d10020 b4 00 00 00 33 c0 5d c2 10 00 8b c0 55 8b ec 83 ....3.].....U... 0x00d10030 c4 e4 53 56 57 8b 5d 10 8b 45 08 8b 90 b4 08 00 ..SVW.]..E...... 0xd10000 55 PUSH EBP 0xd10001 8bec MOV EBP, ESP 0xd10003 8b5510 MOV EDX, [EBP+0x10] 0xd10006 8b450c MOV EAX, [EBP+0xc] 0xd10009 8b4808 MOV ECX, [EAX+0x8] 0xd1000c 898ab8000000 MOV [EDX+0xb8], ECX 0xd10012 8b480c MOV ECX, [EAX+0xc] 0xd10015 898ac4000000 MOV [EDX+0xc4], ECX 0xd1001b 8b4010 MOV EAX, [EAX+0x10] 0xd1001e 8982b4000000 MOV [EDX+0xb4], EAX 0xd10024 33c0 XOR EAX, EAX 0xd10026 5d POP EBP 0xd10027 c21000 RET 0x10 0xd1002a 8bc0 MOV EAX, EAX 0xd1002c 55 PUSH EBP 0xd1002d 8bec MOV EBP, ESP 0xd1002f 83c4e4 ADD ESP, -0x1c 0xd10032 53 PUSH EBX 0xd10033 56 PUSH ESI 0xd10034 57 PUSH EDI 0xd10035 8b5d10 MOV EBX, [EBP+0x10] 0xd10038 8b4508 MOV EAX, [EBP+0x8] 0xd1003b 8b DB 0x8b 0xd1003c 90 NOP 0xd1003d b408 MOV AH, 0x8 0xd1003f 00 DB 0x0 Process: IEXPLORE.EXE Pid: 1740 Address: 0xd20000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00d20000 55 8b ec 83 c4 d0 53 56 57 be 39 05 00 00 8b c6 U.....SVW.9..... 0x00d20010 8b 90 b4 08 00 00 8b 5a 34 8b 83 24 03 00 00 89 .......Z4..$.... 0x00d20020 45 e8 8b 83 ec 03 00 00 05 cd 00 00 00 89 45 e4 E.............E. 0x00d20030 64 ff 35 00 00 00 00 8f 45 ec ff 75 e8 8f 45 f0 d.5.....E..u..E. 0xd20000 55 PUSH EBP 0xd20001 8bec MOV EBP, ESP 0xd20003 83c4d0 ADD ESP, -0x30 0xd20006 53 PUSH EBX 0xd20007 56 PUSH ESI 0xd20008 57 PUSH EDI 0xd20009 be39050000 MOV ESI, 0x539 0xd2000e 8bc6 MOV EAX, ESI 0xd20010 8b90b4080000 MOV EDX, [EAX+0x8b4] 0xd20016 8b5a34 MOV EBX, [EDX+0x34] 0xd20019 8b8324030000 MOV EAX, [EBX+0x324] 0xd2001f 8945e8 MOV [EBP+0xffffffe8], EAX 0xd20022 8b83ec030000 MOV EAX, [EBX+0x3ec] 0xd20028 05cd000000 ADD EAX, 0xcd 0xd2002d 8945e4 MOV [EBP+0xffffffe4], EAX 0xd20030 64ff3500000000 PUSH DWORD [FS:0x0] 0xd20037 8f45ec POP DWORD [EBP+0xffffffec] 0xd2003a ff75e8 PUSH DWORD [EBP+0xffffffe8] 0xd2003d 8f45f0 POP DWORD [EBP+0xfffffff0] Process: IEXPLORE.EXE Pid: 1740 Address: 0xd30000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 1, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00d30000 55 8b ec 81 c4 d0 fe ff ff 53 56 57 89 55 e0 8b U........SVW.U.. 0x00d30010 d8 8b f3 8b 86 b4 08 00 00 89 45 d8 8b 78 34 8b ..........E..x4. 0x00d30020 87 24 03 00 00 89 45 e8 8b 87 e8 03 00 00 05 13 .$....E......... 0x00d30030 01 00 00 89 45 e4 64 ff 35 00 00 00 00 8f 45 ec ....E.d.5.....E. 0xd30000 55 PUSH EBP 0xd30001 8bec MOV EBP, ESP 0xd30003 81c4d0feffff ADD ESP, 0xfffffed0 0xd30009 53 PUSH EBX 0xd3000a 56 PUSH ESI 0xd3000b 57 PUSH EDI 0xd3000c 8955e0 MOV [EBP+0xffffffe0], EDX 0xd3000f 8bd8 MOV EBX, EAX 0xd30011 8bf3 MOV ESI, EBX 0xd30013 8b86b4080000 MOV EAX, [ESI+0x8b4] 0xd30019 8945d8 MOV [EBP+0xffffffd8], EAX 0xd3001c 8b7834 MOV EDI, [EAX+0x34] 0xd3001f 8b8724030000 MOV EAX, [EDI+0x324] 0xd30025 8945e8 MOV [EBP+0xffffffe8], EAX 0xd30028 8b87e8030000 MOV EAX, [EDI+0x3e8] 0xd3002e 0513010000 ADD EAX, 0x113 0xd30033 8945e4 MOV [EBP+0xffffffe4], EAX 0xd30036 64ff3500000000 PUSH DWORD [FS:0x0] 0xd3003d 8f45ec POP DWORD [EBP+0xffffffec] Process: IEXPLORE.EXE Pid: 1740 Address: 0xe40000 Vad Tag: VadS Protection: PAGE_EXECUTE_READWRITE Flags: CommitCharge: 9, MemCommit: 1, PrivateMemory: 1, Protection: 6 0x00e40000 00 00 ac 00 08 00 ac 00 02 10 00 00 01 00 ac 00 ................ 0x00e40010 05 00 ac 00 01 00 ac 00 00 00 00 00 00 00 00 00 ................ 0x00e40020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0x00e40030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 0xe40000 0000 ADD [EAX], AL 0xe40002 ac LODSB 0xe40003 0008 ADD [EAX], CL 0xe40005 00ac0002100000 ADD [EAX+EAX+0x1002], CH 0xe4000c 0100 ADD [EAX], EAX 0xe4000e ac LODSB 0xe4000f 000500ac0001 ADD [0x100ac00], AL 0xe40015 00ac0000000000 ADD [EAX+EAX+0x0], CH 0xe4001c 0000 ADD [EAX], AL 0xe4001e 0000 ADD [EAX], AL 0xe40020 0000 ADD [EAX], AL 0xe40022 0000 ADD [EAX], AL 0xe40024 0000 ADD [EAX], AL 0xe40026 0000 ADD [EAX], AL 0xe40028 0000 ADD [EAX], AL 0xe4002a 0000 ADD [EAX], AL 0xe4002c 0000 ADD [EAX], AL 0xe4002e 0000 ADD [EAX], AL 0xe40030 0000 ADD [EAX], AL 0xe40032 0000 ADD [EAX], AL 0xe40034 0000 ADD [EAX], AL 0xe40036 0000 ADD [EAX], AL 0xe40038 0000 ADD [EAX], AL 0xe4003a 0000 ADD [EAX], AL 0xe4003c 0000 ADD [EAX], AL 0xe4003e 0000 ADD [EAX], AL
$ ./vol.py -f ~/cuckoo/storage/analyses/10/memory.dmp poisonivyconfig -p 1740
Volatile Systems Volatility Framework 2.3_alpha
------------------------------------------------------------
Process: IEXPLORE.EXE (1740)
Infection:
PoisonIvy has ADMIN privileges!
Version: 231
Base VA: 0x00150000
Extra VA: 0x00c20000
Data VA: 0x00160000
Mutex: nrnr999rn
Original file: C:\DOCUME~1\cooks\LOCALS~1\Temp\ce69dee5307d58db4e2a6fdbcbf87e9d
Melt original file: ON
Command and Control:
Host 01: sendmsg.jumpingcrab.com:443 (direct)
Host 02: sendmsg.jumpingcrab.com:80 (direct)
Password: menuPass
Id: 10.8sendmsg.jumpingcrab.com
Group:
Keylogger:
Keylogger: off
Copy file:
Copy routine: 0x01130000
Destination: %WINDIR%\System32:MCPUPlayer.exe
Persistence:
Active Setup: off
HKLM Run: ON
HKLM Run name: AdobeCro CPUPlayer
Setup routine: 0x00c10000
Injector:
Inject into other processes: ON
Persistently: ON
Injector TID: 0
Injector Routine: 0x00000000
Target process name:
Target default browser: ON
Based on the VirusTotal results supplied with Cuckoo's analysis, only Trend Micro identified the Upclicker sample as Poison Ivy (BKDR_POISON.BNE). The other 44 engines either failed to detect anything (22/45 ratio) or identified it as a generic backdoor.
Conclusion
Now that you've reached the end, you know that Trojan Upclicker is a wrapper/packer that in this case transmitted Poison Ivy as its payload. Cuckoo Sandbox can be easily modified to fit your analysis needs, even if you're a first time user. Starting with 0.5, it can be configured to acquire full memory dumps - thus it gets along quite nicely with Volatility's new VirtualBoxAddressSpace for those who wish to go deep diving in memory after an infection. You've also seen some recent malware leveraging the GUI subsystem to further its malicious intentions, which is always exciting.





No comments:
Post a Comment