Instructors: Michael Ligh (@iMHLv2), Andrew Case (@attrc), Jamie Levy (@gleeda)
To request a link to the online registration site or to receive a detailed course agenda/outline, please send an email voltraining [[ at ]] memoryanalysis.net.
We have some more feedback from our Amsterdam class to share with you:
"An excellent technical malware course, highly recommended!" - Tom (Price Waterhouse Cooper)
"I find I have much more ways of success in my work with malware analysis. Volatility is a great tool, keep up the good work!!!" - Goran (CERT-SE)
"Great contents, expert teachers, hands on examples" - Boudewijn (NCSC-nl)
"It was great experience and mind blowing info. The thing I appreciated the most were the graphics to help with visualisation and putting the Windows internals info in a goal and purpose view." - Anonymous
"I think this is a really nice course and the best course I have had so far" - Monnappa (Cisco)
As always, we constantly update our course materials and this course will include new modules on Windows 8 and structured memory analysis of TrueCrypt.These represent some of the latest advances in memory forensics, and by taking the class you can be among the first to learn the new skills firsthand.
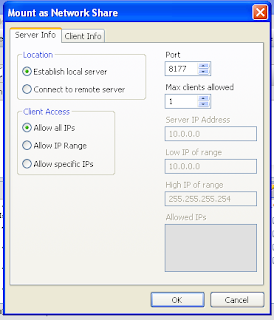
This is the only memory forensics course officially designed, sponsored, and taught by the Volatility developers. One of the main reasons we made Volatility open-source is to encourage and facilitate a deeper understanding of how memory analysis works, where the evidence originates, and how to interpret the data collected by the framework's extensive set of plugins. Now you can learn about these benefits first hand from the developers of the most powerful, flexible, and innovative memory forensics tool.
If studying in the "Big Apple" doesn't suit you remember that we also have offerings in San Diego, CA (January 20th - 24th) and London, UK (June 9th - 13th) in 2014!